Critical infrastructure security is in the national spotlight.[1] According to the 2022 State of Operational Technology and Cybersecurity Report, organizations throughout the world’s OT security initiatives are making inadequate progress toward comprehensive protection of ICS and SCADA systems in the relatively new world of connected OT.[2] The Biden administration recently issued a national security memorandum that sets baseline cybersecurity goals and practices to protect the grid. The order also encourages the deployment of advanced technology for threat visibility, detection, monitoring, and response.
Power and utility companies play a starring role in safeguarding the nation’s infrastructure. As organizations double down on compliance and technology, there are several things to consider amidst a rapidly evolving cybersecurity landscape.
CONFIDENTIALITY–INTEGRITY–AVAILABILITY (CIA) TRIAD
The CIA Triad is a data security concept. It directs a company’s data security efforts and helps lay out a strong security foundation. In fact, including these ideas in any security program is ideal. The three pillars of security architecture are:
Confidentiality
In today’s world, it is critical for people to protect their sensitive private information from unauthorized access. Protecting confidentiality necessitates the ability to define and enforce specific levels of access to information. In some cases, this entails categorizing information into different collections based on who needs access to the information and how sensitive the data is — the amount of damage suffered if confidentiality is breached. Access control lists, volume and file encryption, and Unix file permissions are some of the most used methods for managing confidentiality.
Integrity
The “I” in the CIA triad represents data integrity. This critical component of the CIA Triad is intended to prevent data from being deleted or modified by unauthorized parties. For example, online buyers demand accurate product and pricing information and assurances that the quantity, cost, availability, and other information will not change after they make their order. Data integrity safeguards include encryption, hashing, digital signatures, and digital certificates.
Availability
The availability of your data is the focus of this stage — the third in the CIA Triad. High-availability systems are computing resources with architectures specifically designed to increase availability. The most well-known attack that jeopardizes availability is called a denial-of-service attack, in which a system, website, or web-based application’s performance is purposely and maliciously compromised or the system is rendered inaccessible. The breakdown of hardware or software, power outages, natural catastrophes, and human error are other possible risks to availability. The information must be protected and made available when needed, which requires that authentication procedures, access routes, and systems all function effectively.
The CIA Triad is all about information and data security. But the first thing to note in Figure 1 is that, in general, IT and OT risk management priorities differ. IT prioritizes confidentiality, while OT prioritizes availability, followed by integrity and confidentiality (A-I-C). It is critical for every business to identify these priorities since they determine the overall security defensive systems of the organization.
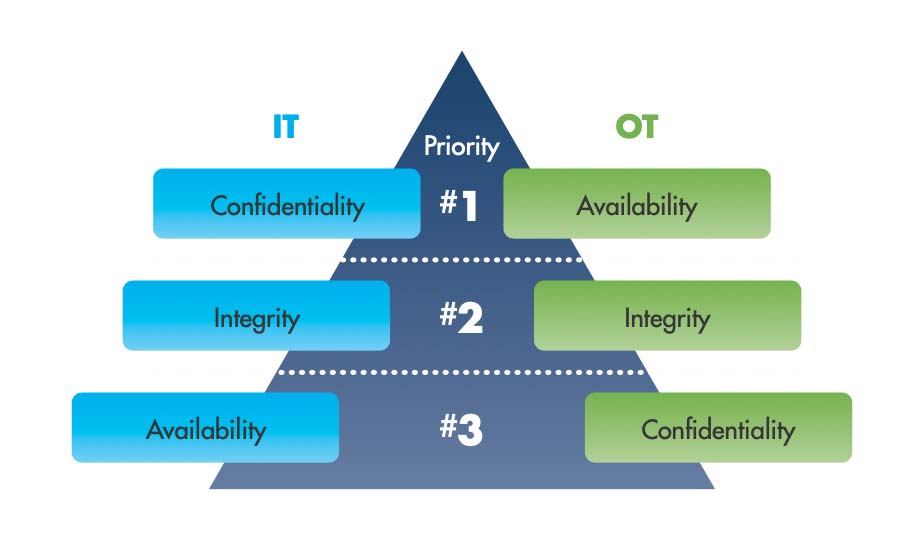
Figure 1: CIA Triad Priorities
OT SECURITY GOVERNANCE[3]
The federal government has issued many executive orders in the past to strengthen the cybersecurity posture of vital infrastructure. President Biden most recently signed Executive Order 14028 Improving the Nation’s Cybersecurity in May 2021 to protect critical infrastructure.[4] This directive focuses on modernizing cybersecurity requirements such as data encryption at rest and in transit, a zero-trust architecture, and the deployment of multifactor authentication and data encryption within a certain timeframe.
This demonstrates that even today, having a basic security foundation such as the NIST Cybersecurity Framework (CSF), which went into force nearly a decade ago, is vital for critical infrastructure organizations. The NIST CSF consists of a framework core, profiles, and implementation tiers. While the core functions of the NIST CSF include categories, subcategories, and informative references, we will focus on the first two core components shown in Figure 2 of this framework from a 1,000-foot perspective.
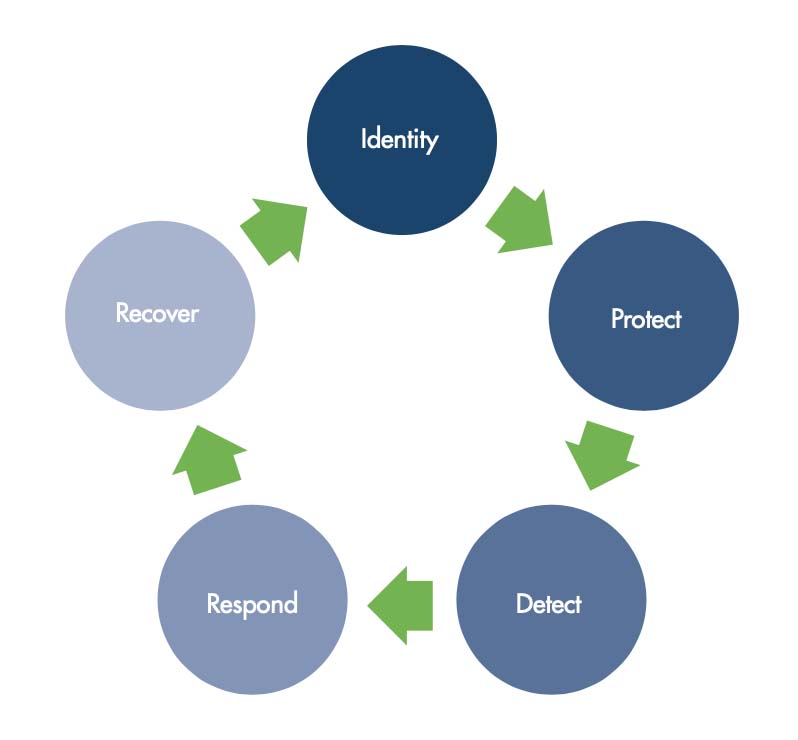
Figure 2: NIST Cybersecurity Framework
Asset management, a comprehensive inventory of all OT assets, is one of the essential core components of an OT asset database — not only hardware, but also a comprehensive view of the data, personnel, devices, systems, and facilities that enable the organization to meet its objectives. They must be identified, and their importance in business objectives and risk management must be clearly established. Database management software can bridge the divide between competing IT and OT priorities. Look for a relational database architecture that will support a central data warehouse structured for universal interfacing to external systems. Bringing such a system on-line will integrate OT data into a hub where asset management and work management will intersect.
Connecting dataflows emanating from different sources enables OT teams to have the data integrity, availability, and confidentiality they prioritize while critical elements related to human performance and network security remain intact for IT intents and purposes. The ideal OT database management system will accept user authentications developed in the IT domain, which complements the corporate cybersecurity measures put in place for user (and device) password management. This assures data security and integrity as well.
After identifying and categorizing your assets, you should take proactive measures to safeguard them from internal and external cyber threats. Security maintenance rules and practices, including software patch management and whitelisting, must be created and implemented for the NIST CSF’s Protect component.
INVEST IN TRANSIENT CYBER ASSET SECURITY AND PATCH MANAGEMENT
Remote field devices can present major security risks. Transient cyber assets (TCAs) such as tablets, asset testing laptops, and protective relays are often disconnected from the main network, making them a prime channel for spreading malware. Given that TCAs regularly contact critical assets, they’re a top security threat if not secured properly. Speed is of the essence when it comes to cybersecurity.
However, securing your assets shouldn’t hold productivity back. Look for systems you can tailor to secure the work processes that need defenses the most and streamline procedures from the field to the office. Tapping patch management software that easily shows the patch updates available to TCAs enables you to quickly select the updates you want and automatically downloads those installers to TCAs to be installed during remote updates. Patch management systems should also monitor, send alerts, and report on security risks, keeping you in a constant state of vigilance.
STAY PREPARED AND PROACTIVE
Cyber threats are fast moving and unpredictable. Utilities need to be armed and ready with the right tools and processes. While advanced technology for threat identification and management is currently strongly encouraged by the Biden administration, it could soon become a requirement.
REFERENCES
1. Fortinet. 2022 State of Operational Technology and Cybersecurity Report. Accessed at https://www.fortinet.com/content/dam/fortinet/assets/analyst-reports/report-2022-ot-cybersecurity.pdf.
2. Whitehouse.gov. National Security Memorandum on Improving Cybersecurity for Critical Infrastructure Control Systems, 2021. Accessed at https://www.whitehouse.gov/briefing-room/statements-releases/2021/07/28/national-security-memorandum-on-improving-cybersecurity-for-critical-infrastructure-control-systems/.
3. G. Meghan. What is the NIST Cybersecurity Framework? Verve Blog, 2022. Accessed at https://verveindustrial.com/resources/blog/what-is-the-nist-cybersecurity-framework/.
4. Whitehouse.gov. Executive Order on Improving the Nation’s Cybersecurity, 2021. Accessed at https://www.whitehouse.gov/briefing-room/presidential-actions/2021/05/12/executive-order-on-improving-the-nations-cybersecurity/.
 Bryan J. Gwyn is Senior Director of Solutions at Doble, with over 30 years of international experience in electric utility transmission and distribution protection and control and telecommunication engineering, operations and management. Leading a team of global subject matter experts, he is responsible for the development of protection, asset management, monitoring, and security solutions. Bryan received his BEng (Hons) in electrical and electronic engineering and his PhD at City University, London. He is a Chartered Engineer and a Senior Member of IEEE.
Bryan J. Gwyn is Senior Director of Solutions at Doble, with over 30 years of international experience in electric utility transmission and distribution protection and control and telecommunication engineering, operations and management. Leading a team of global subject matter experts, he is responsible for the development of protection, asset management, monitoring, and security solutions. Bryan received his BEng (Hons) in electrical and electronic engineering and his PhD at City University, London. He is a Chartered Engineer and a Senior Member of IEEE.
 Sagar S. Singam is a Senior Cyber Security Engineer at Doble with more than 8 years of expertise in industrial and IT cybersecurity architecture. He obtained his MS in information assurance and cybersecurity from Regis University.
Sagar S. Singam is a Senior Cyber Security Engineer at Doble with more than 8 years of expertise in industrial and IT cybersecurity architecture. He obtained his MS in information assurance and cybersecurity from Regis University.
